Cat Videos

Long ago and far away, I worked for a company that wanted to take its perfectly cute and googly icon, and change it into something sharp and angular and unapproachable. I had started my big tech career working for a company that stood its ground behind Duke the Java Mascot, who was created by a […]
Being Precise in our Language Usage

I wrote this letter to the leadership of a European client of ours. Our role was specifically to ensure that accurate American English was being used in reports for the US. I had discovered that they did not see a difference between terms, and were therefore using them very, very incorrectly. So incorrectly that it […]
Supportability as Software with MinIO SUBNET
This was a bespoke piece I wrote for MinIO back in 2022 Tl;dr MinIO leverages engineering focus and minimalist thinking to add supportability functionality, which means finding and fixing issues before they become problems in your installation. Going Beyond: Supportability as Software in MinIO In the same way that DevOps and Cloud Native require a […]
Business Continuity/Disaster Recovery (BC/DR)

When discussing disasters and recovery from them, it’s often a hard sell, just based on numbers. That’s unfortunate, because the first casualty of downtime is your credibility as a corporation. It’s important to be clear on the idea that cost of backup/replication will never be higher than the costs of business lost due to poor BC/DR planning.
Passive Voice and Hacker Zombies

Originally published April 18, 2018 | Laureen Hudson Note: this is a repost of a blog I wrote back in 2018, working for the late, great AlienVault in their Content department. Any references to AlienVault Editorial should be assumed to be in past tense. Passive voice in written communication is a huge part of the InfoSec […]
Cambridge Analytica Debacle – The Definition Of Breach

Originally published March 20, 2018 | Laureen Hudson Note: this is a repost of a blog I wrote back in 2018, working for the late, great AlienVault in their Content department. Any references to AlienVault Editorial should be assumed to be in past tense. Pretty much the motto of my profession is “word choice matters.” I say […]
Infosec Language Grows Up: The Bishop Fox Cybersecurity Style Guide

Originally published March 13, 2018 | Laureen Hudson Note: this is a repost of a blog I wrote back in 2018, working for the late, great AlienVault in their Content department. Any references to AlienVault Editorial should be assumed to be in past tense. On February 15, Bishop Fox released their Cybersecurity Style Guide. I am absolutely […]
When Bad Language Happens To Good Systems

Originally published January 25, 2018 | Laureen Hudson Note: this is a repost of a blog I wrote back in 2018, working for the late, great AlienVault in their Content department. Any references to AlienVault Editorial should be assumed to be in past tense. In my last blog, I wrote about how words are created and then […]
Shakespeare’s Netymology

Originally published January 18, 2018 | Laureen Hudson Note: this is a repost of a blog I wrote back in 2018, working for the late, great AlienVault in their Content department. Any references to AlienVault Editorial should be assumed to be in past tense. One of the coolest things about editing in the tech space, for […]
Cryptocurrency Isn’t Crypto
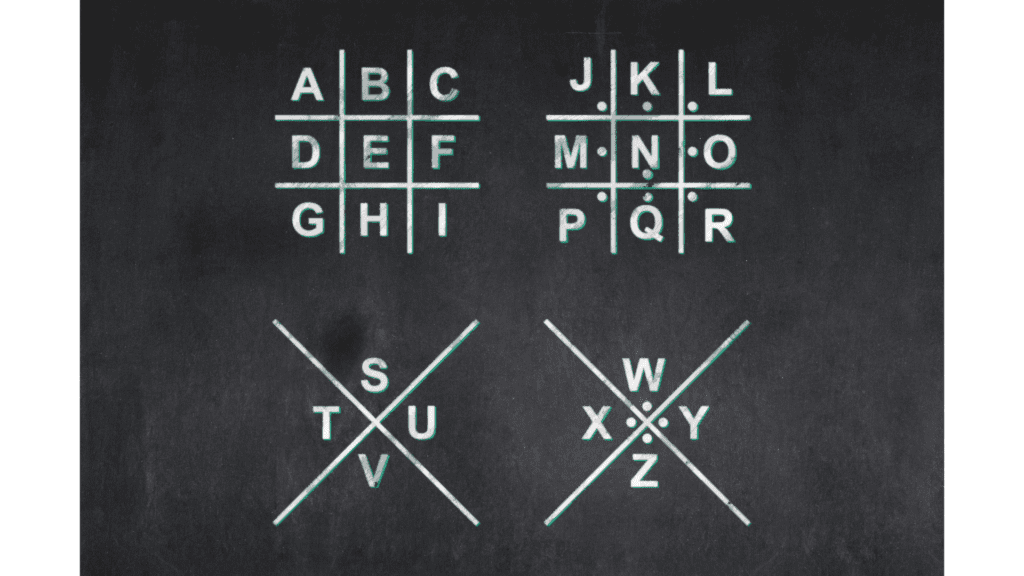
Originally published January 11, 2018 | Laureen Hudson Note: this is a repost of a blog I wrote back in 2018, working for the late, great AlienVault in their Content department. Any references to AlienVault Editorial should be assumed to be in past tense. For the love of all things glittery, you guys, here I am […]
